With the increasing number of cyber threats and attacks, it has become imperative for businesses to prioritize cybersecurity measures. AWS WAF (Web Application Firewall) offers a robust solution to protect your web applications and APIs from malicious activities. By leveraging AWS WAF, you can fortify your security posture and stay one step ahead of hackers. In this article, we will explore how AWS WAF can enhance your cybersecurity defenses and provide effective protection for your digital assets.
Table of Contents
Understanding AWS WAF
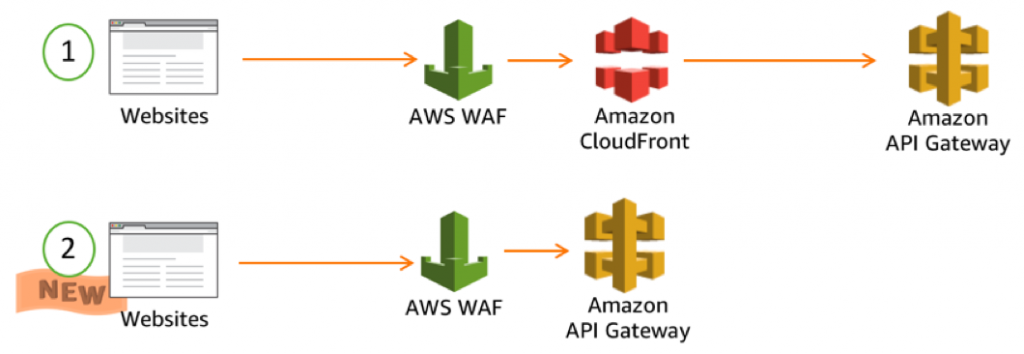
AWS WAF is a cloud-based firewall service that helps safeguard your web applications and APIs against common web exploits and attacks. By analyzing incoming requests, AWS WAF can block malicious traffic, detect and filter out common attack patterns, and protect your applications from common vulnerabilities. Its intuitive interface and seamless integration with other AWS services make it a powerful tool for managing your security controls.
Key Benefits of AWS WAF
By implementing AWS WAF, you gain several key advantages in enhancing your cybersecurity defenses. Firstly, AWS WAF offers comprehensive protection against common web application threats, such as SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks. With its customizable rule sets and real-time monitoring, you have the flexibility to create tailored security policies and adapt to evolving threats. Secondly, AWS WAF integrates seamlessly with other AWS services, such as AWS CloudFront and AWS Application Load Balancer, enabling you to deploy a multi-layered security architecture. Lastly, AWS WAF provides detailed visibility and logging, allowing you to analyze traffic patterns, identify potential risks, and take proactive measures to mitigate threats.
Getting Started with AWS WAF
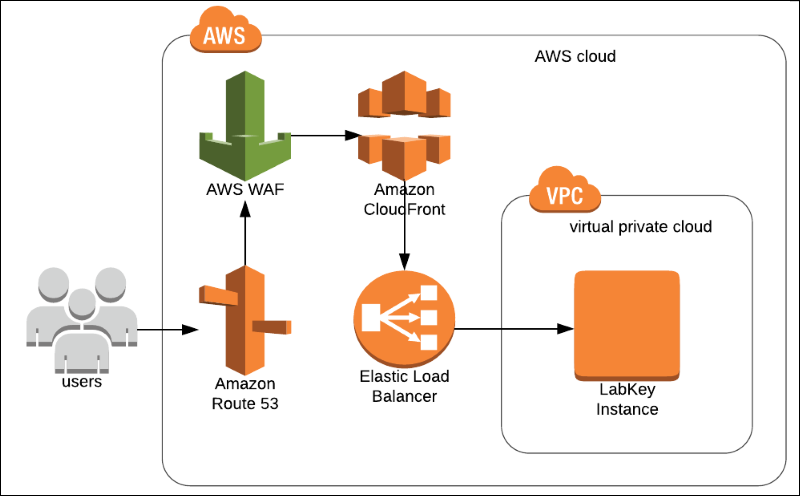
To leverage the power of AWS-WAF, you need to follow a few essential steps. First, you need to set up a WebACL (Web Access Control List), which acts as a rule set for filtering and allowing traffic. Within the WebACL, you can define conditions, rules, and actions to control which requests are allowed or blocked. Next, you can integrate AWS-WAF with your web application or API by associating the WebACL with the appropriate AWS resources, such as CloudFront distributions or Application Load Balancers. AWS-WAF provides a user-friendly console and API interface to configure and manage your security policies effectively.
Advanced Capabilities of AWS-WAF
AWS-WAF offers advanced capabilities that enable you to enhance your cybersecurity posture further. Firstly, you can create custom rules to address specific application vulnerabilities and attack patterns unique to your environment. By combining rule conditions and logical operators, you can build complex rules tailored to your specific requirements. Secondly, AWS-WAF supports rate-based rules to protect against DDoS attacks by limiting the number of requests from a particular IP address. This helps mitigate the impact of bot traffic and brute-force attacks. Lastly, AWS-WAF integrates with AWS Firewall Manager, allowing you to manage multiple accounts and automate rule deployments across your organization.
Real-Time Monitoring and Automated Threat Response

AWS-WAF provides real-time monitoring and logging capabilities, enabling you to gain insights into incoming traffic and potential threats. You can leverage AWS CloudWatch to set up alarms and receive notifications when specific security events occur. Additionally, AWS-WAF integrates with AWS Lambda, allowing you to automate responses to identified threats. For example, you can configure Lambda functions to block IP addresses or send notifications to your security team when suspicious activities are detected. This automated threat response helps you reduce the time to detect and respond to security incidents, enhancing your overall cybersecurity posture.
Scalability and Flexibility with AWS-WAF
One of the significant advantages of AWS-WAF is its scalability and flexibility. As your web traffic grows or changes, AWS-WAF can seamlessly scale to handle increased demands. With its global presence and integration with AWS services, you can deploy AWS-WAF across multiple regions to ensure consistent protection for your applications. AWS-WAF also supports AWS CloudFormation, allowing you to define your security policies as code, automate deployments, and ensure consistency across environments. This flexibility enables you to adapt your security controls as your applications evolve, ensuring continuous protection against emerging threats.
AWS WAF Best Practices
To maximize the effectiveness of AWS WAF, it’s crucial to follow best practices. First and foremost, regularly update your rule sets to stay up-to-date with the latest threats and vulnerabilities. AWS provides managed rule sets that are continuously updated to protect against common attack patterns. Additionally, analyze your logs and metrics to identify any anomalies or suspicious activities. This will help you fine-tune your security policies and ensure accurate detection of threats. Furthermore, leverage AWS WAF’s integration with other AWS services, such as AWS CloudFront and AWS Firewall Manager, to establish a comprehensive and cohesive security architecture.
Conclusion
In the ever-evolving landscape of cybersecurity, staying one step ahead of hackers is essential for safeguarding your digital assets. AWS WAF empowers organizations to bolster their security defenses by providing a powerful and flexible web application firewall solution. By leveraging AWS WAF’s advanced capabilities, real-time monitoring, and automated threat response, you can effectively protect your web applications and APIs against a wide range of threats. Remember to follow best practices and regularly update your security policies to adapt to emerging threats. With AWS WAF, you can level up your cybersecurity game and ensure the integrity, availability, and confidentiality of your digital assets.
Learn about: Engage Unparalleled Defense with Cyber Tanks: A Revolutionary Solution to Modern Security Threats